As per the latest software testing trends that we have been observing in the Quality Assurance (QA) industry, cyber security testing services have become one of the most sort-after and critical requirements in our customer’s QA testing strategy. The increasing number of instances of data thefts, privacy breaches and security vulnerabilities that business and enterprises are facing today has made the importance of security testing services even more critical. To ensure that we are able to efficiently and reliably address our customer’s security testing needs, CredibleSoft practices use of latest industry standards and security testing methodologies.
Advantages and Benefits of Hiring the Best Security Testing Services Company
Information security is a serious challenge that businesses worldwide face today. It is important that security challenges are addressed promptly and expertly, in order to avoid the consequences such as loss of business profit or damaged brand reputation. By making sure your application was subjected to expert vulnerability assessment and penetration testing (VAPT), you can have the following advantages and benefits.
 – EFFECTIVE RISK MANAGEMENT. This provides a baseline to work with in order to address the security risks in a reliable and structured way.
– EFFECTIVE RISK MANAGEMENT. This provides a baseline to work with in order to address the security risks in a reliable and structured way.
– ENSURE BUSINESS CONTINUITY. A secure application with close-to-zero vulnerability will be essentially less prone to hacking attacks. This results in enhanced business continuity.
– ENSURE PROTECTION OF CLIENTS, PARTNERS, END USERS. It is imperative for every business organizations to not only protect their own data, information and assets, but also to ensure protection of assets of its clients, partners and end-users.
– PROTECT BRAND REPUTATION. Employing a security testing company to assess your application’s security helps protect against loss of your brand’s reputation. It is important to note that while it takes years of hard work to build your brand value and reputation, the same can be damaged within minutes by a single hacking attack or data theft episode.
Why Choose CredibleSoft as Your Penetration Testing Services Provider Company?
We at CredibleSoft, offer an rigorous automated testing and manual vulnerability assessment and security testing service to track down security vulnerabilities in your software applications. Our penetration testing experts are highly experienced and certified. We use some of the latest proprietary tools from security testing industry leaders such as HP, IBM, McAfee and Symantec to execute our vulnerability scanning and security testing processes.
Our Proven Security Testing Framework Enables Our Customers To:
– Perform web application security audit (as per OWASP standards) of their applications.
– Conduct vulnerability scanning to identify vulnerabilities in their business critical applications.
– Integrate penetration testing and vulnerability analysis as part of their application development life cycle.
– Use open-source as well as commercially available security testing tools.
– Avail security testing services while choosing from flexible pricing models of engagement.
Key Objectives of Our Offshore Security Testing Services:
– Certification of builds/applications as per popular security standards.
– Develop a streamlined process and reliable model for application security testing, vulnerability assessment and risk-modeling.
– Build a framework of re-usable security testing artifacts.
– Leverage our proprietary security testing jump-start kits for faster time-to-market.
Key Service Offerings of Our Offshore Security Testing:
– Vulnerability scanning and security auditing.
– Security Compliance Certification of builds/applications.
– An end-to-end security testing services catalog that is capable of providing an integrated security testing approach for all applications (mobile, web, client-server, etc) security testing.
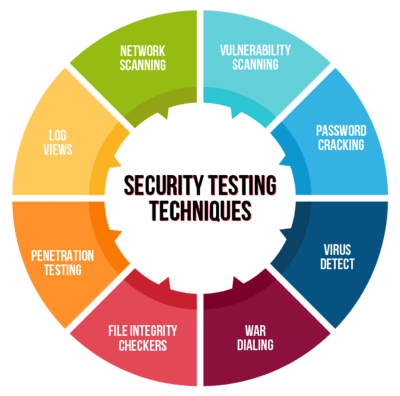
Key Features of CredibleSoft’s Security Testing Services
We offer a comprehensive range of vulnerability assessment, penetration testing and security testing services that includes the following:
– Vulnerability Assessment
– Web Application Security
– Mobile Application Security
– Social Engineering
– Cross-Site Scripting (XSS)
– Cross-Site Request Forgery (CSRF)
– SQL Injection, URL Injection
– PCI DSS
– Distributed Denial of Services (DDOS) Assessment
– Broken Authentication and Insecure Session Management
– Insecure Direct Object Reference
– Server-side Security Misconfigurations
– Failure to Restrict URL Access
– Insufficient Transport Layer Protection
– Unvalidated Redirects and Forwards